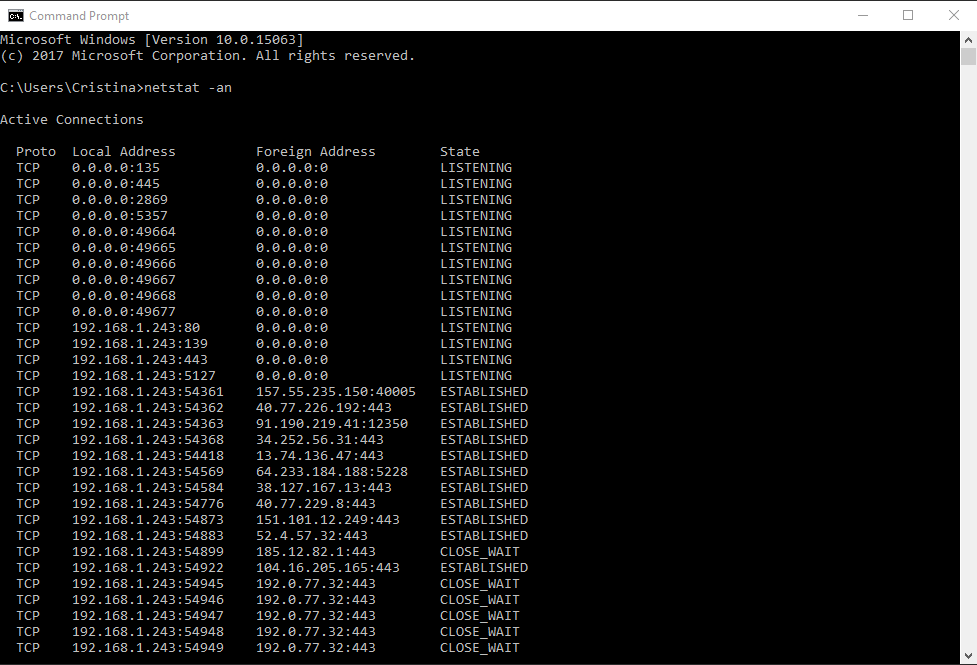
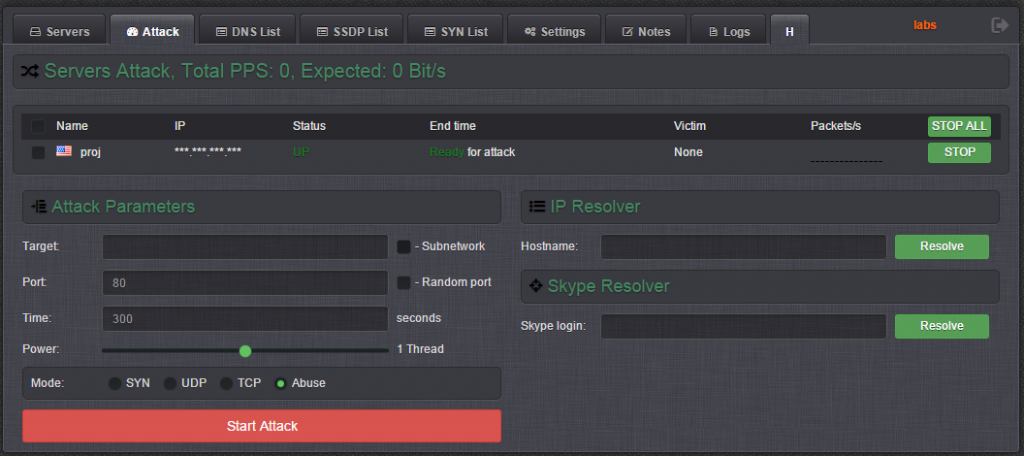
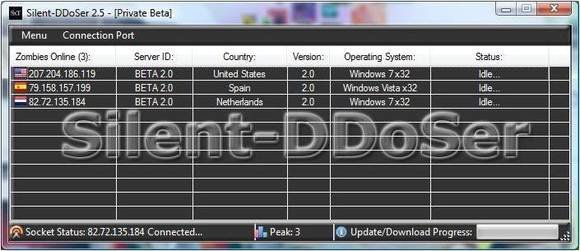
How NETSCOUT built a global DDoS awareness platform with Amazon OpenSearch Service | AWS Big Data Blog
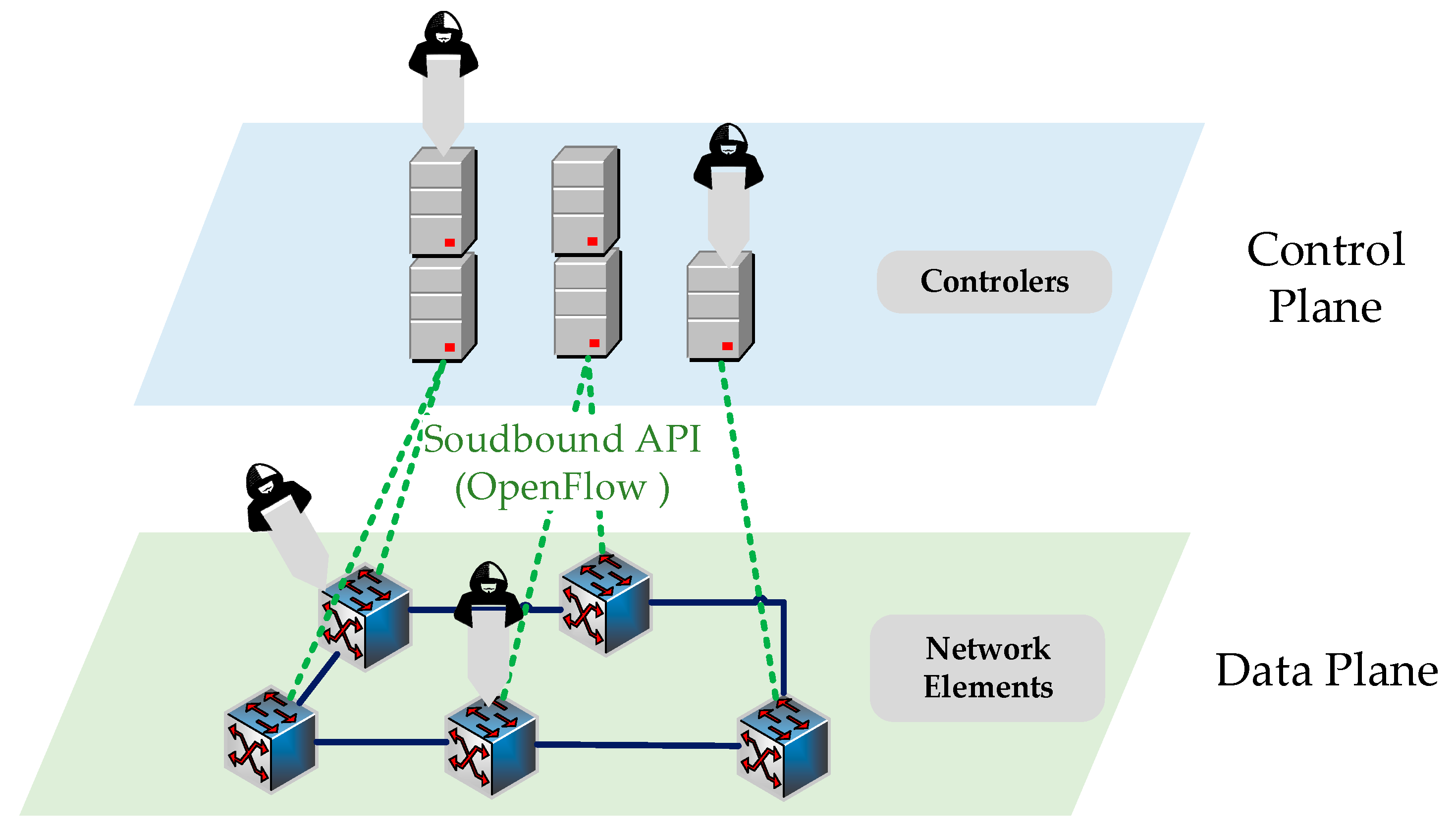
Sustainability | Free Full-Text | Detecting DDoS Attacks in Software-Defined Networks Through Feature Selection Methods and Machine Learning Models