Sandisk 32 GB USB Flash Drive - SDIX30N-032G-GNAOA : Buy Online at Best Price in KSA - Souq is now Amazon.sa: Electronics

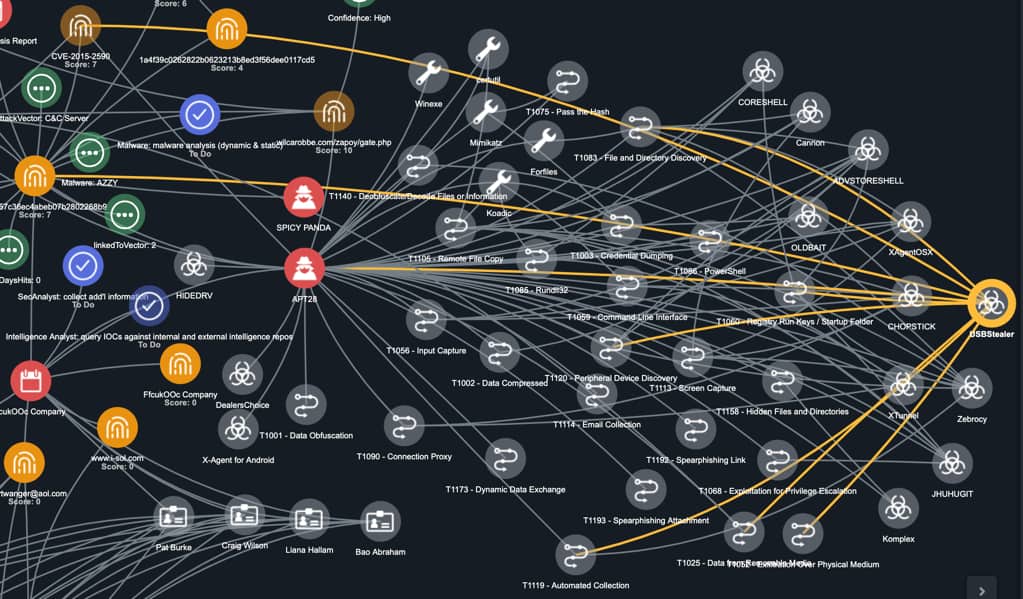
USB Stealer, Just like those unrealistic movies and TV shows, except this one's real. - Leewardslope

Amazon.co.jp: USB Drive Portable USB Flash Drive Business Trip Travel Work School Home (#3) : Computers










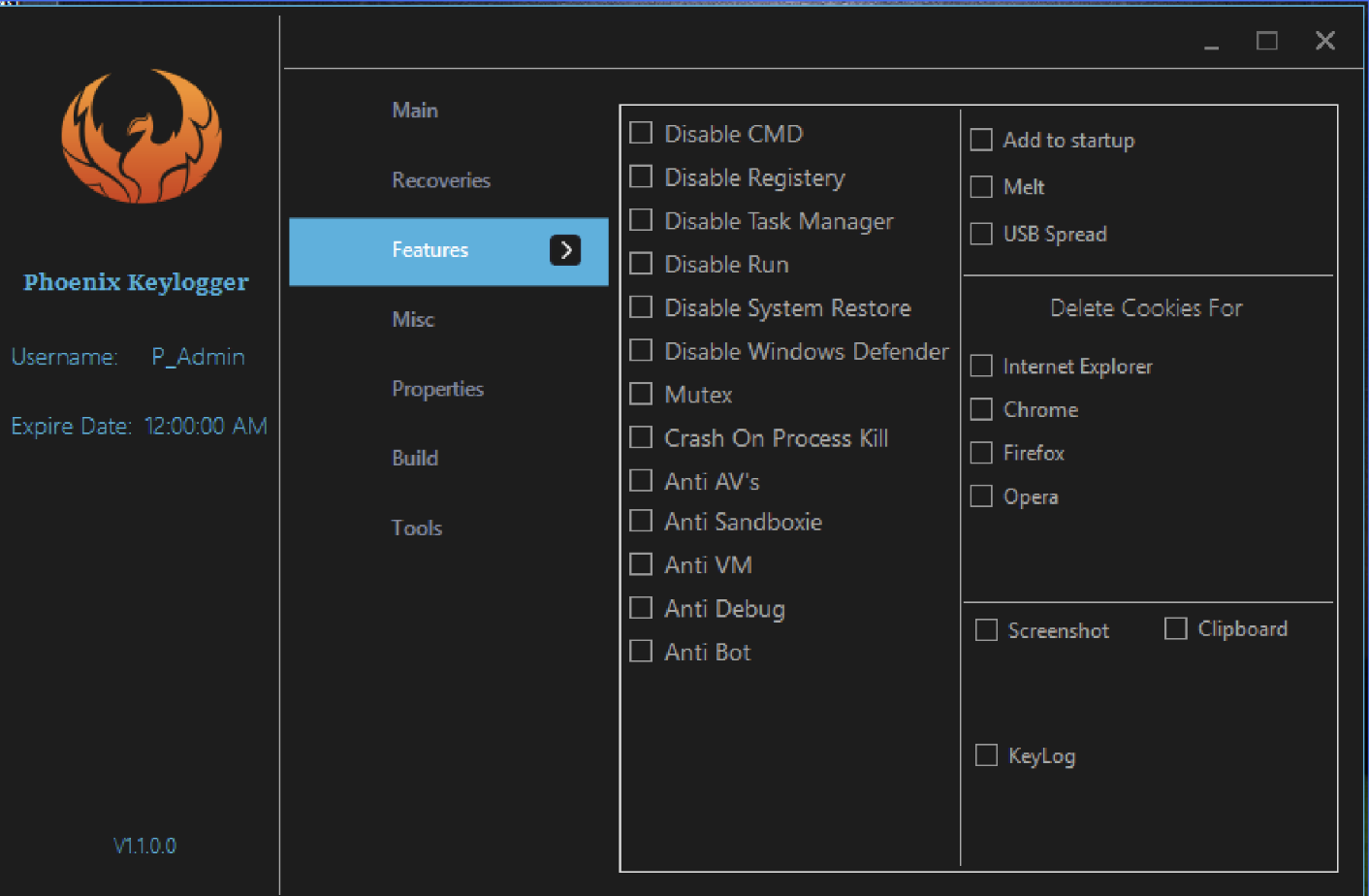


/cdn.vox-cdn.com/uploads/chorus_asset/file/23949203/226141_rubberDucky.jpg)